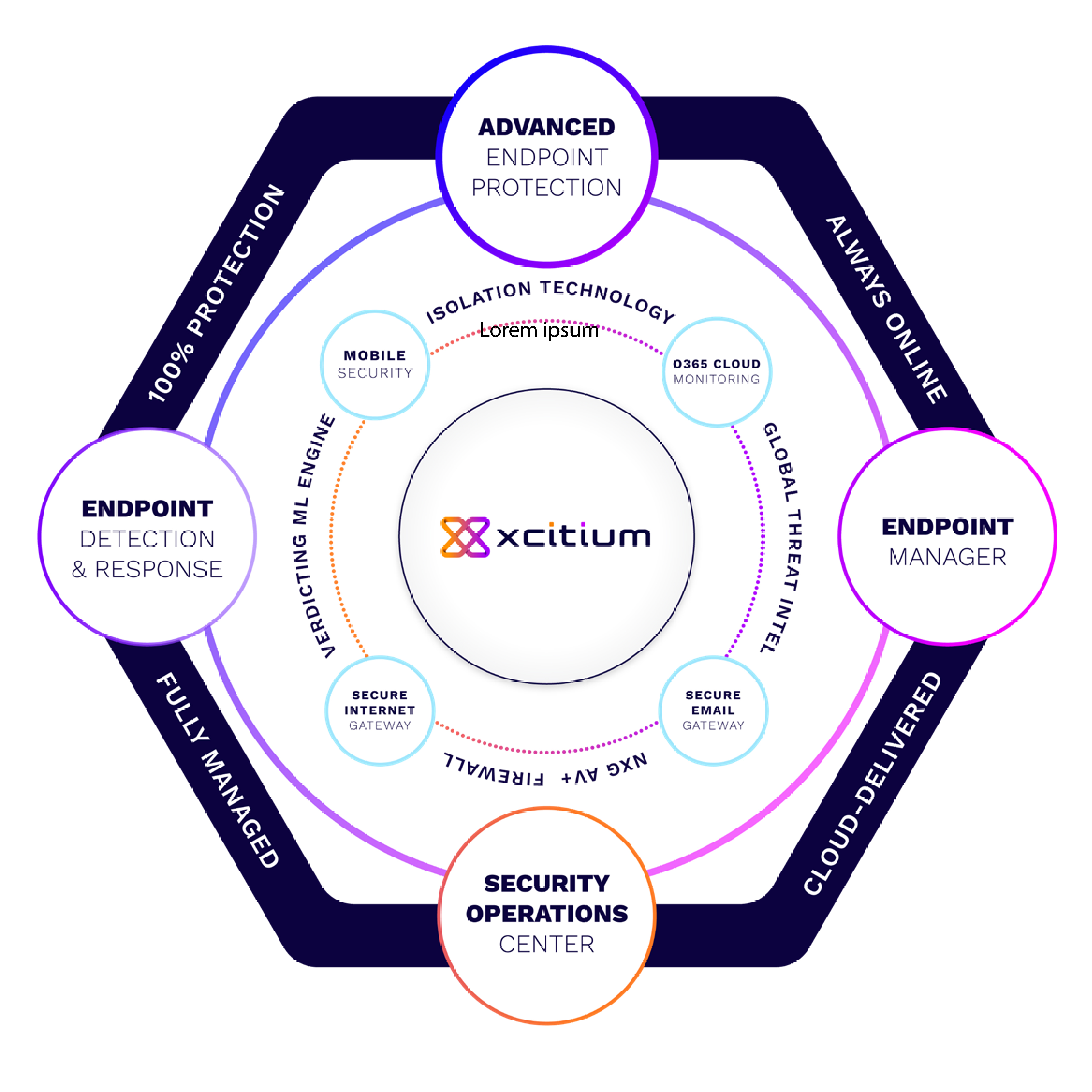
Cybersecurity Consulting in Malaysia
Endpoint Protection Kernel API Virtualization The Cyber Intrusion Kill Chain, aka Kill Chain, was adapted from military concepts. Lockheed Martin’s engineers were the first to apply it to cyber security attack stages. The core,.,